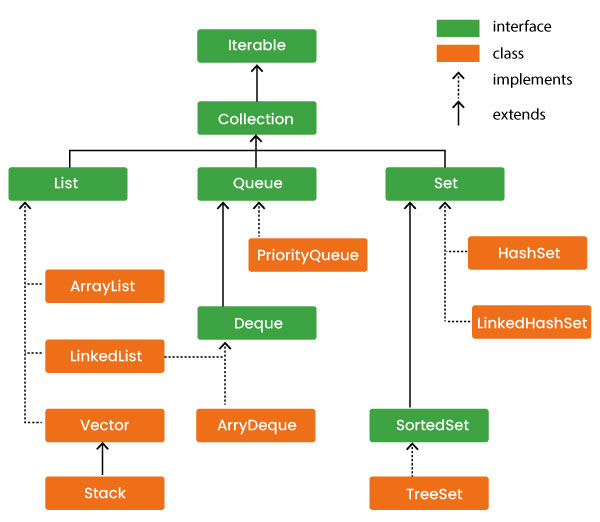
Graph
Graph
DFS
Find connected components, check for cycles
261. Graph Valid Tree
Undirected graph, check if it’s acyclic and connected.
Using vis[i]=True is sufficient. However, since it’s an undirected graph, when traversing neighbors, you need to skip the parent node, so it needs to be passed as a parameter.